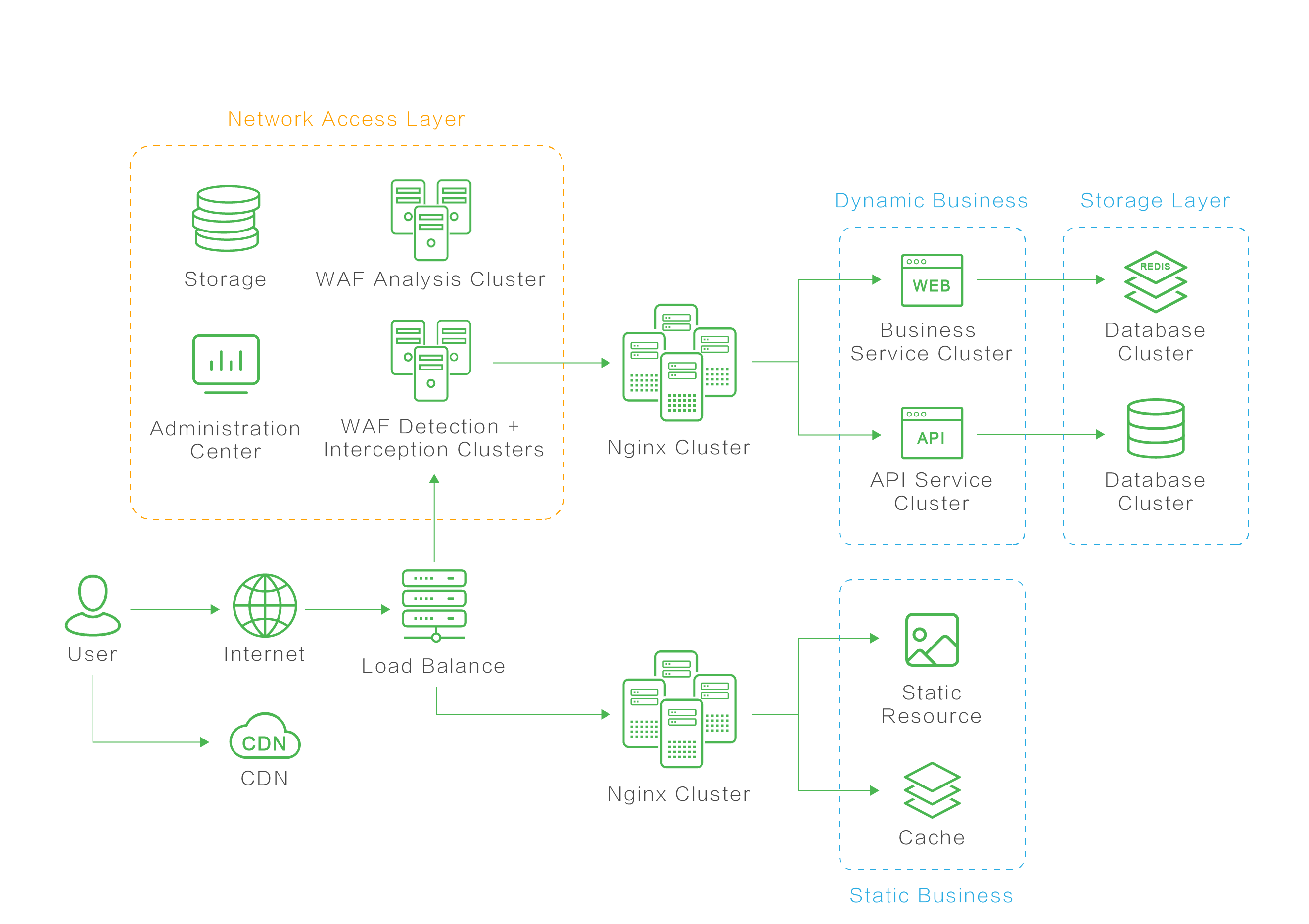
Web 2.0 has pluralistic development of network behavior. Business development and users increase further improved the performance requirements of the website. The bottleneck of any link will affect the normal business operation of the website system and user experience, then cause huge economic losses. High-traffic websites are confronted with nonnegligible rigid demands.
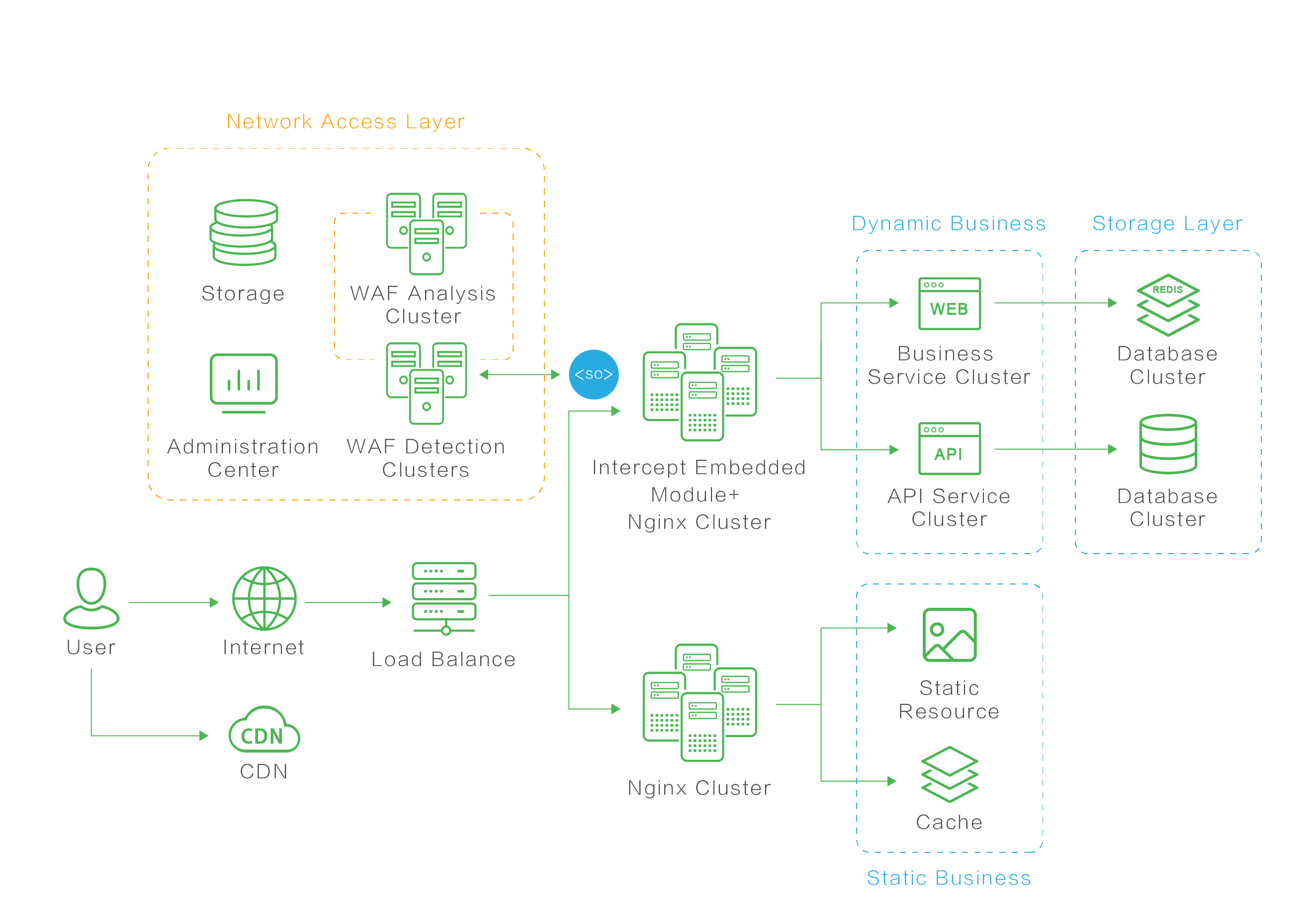
Chaitin in-depth researches enterprise utilize scenarios based on rich practical experience, and forms a set of web application security solutions for high-traffic website architecture. It can meet the requirements of architecture and realize the dual protection of application security and business security.
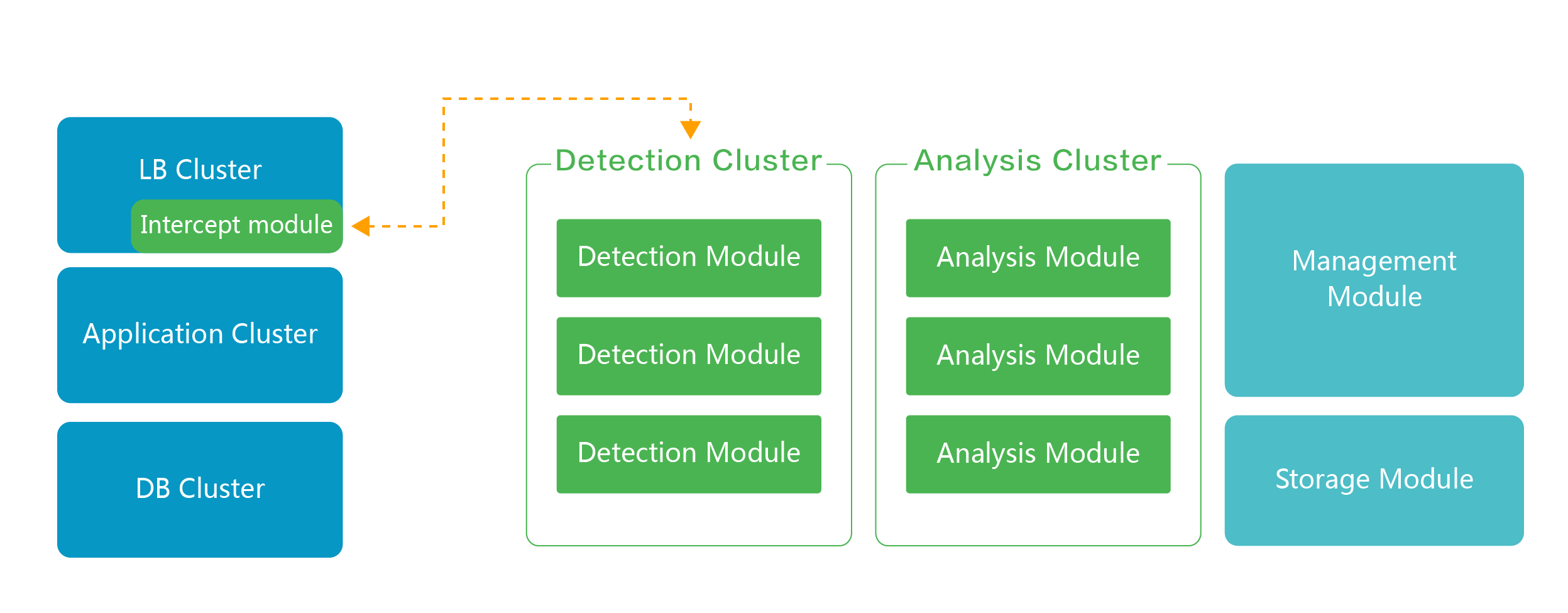
The software cluster deployment solution modularizes functions, which can deploy different functional components to specific servers and combine them according to the actual needs of enterprises, so as to maximize the utilization of service resources to meet the requirements of large traffic, high concurrency and extensible.
It supports two kinds of cluster deployment modes with excellent horizontal expansion. In theory, it can support unlimited concurrent processing capacity, which can be extended according to the real business traffic to solve the deployment requirements of high-traffic website architecture.
The intelligent semantic algorithm doesn’t use the traditional rule database, and has high accuracy, low false positive rate, highest level of attack interception in the world.
Innovative intelligent algorithm with extremely accurate interception and low false positive rate.
Modularize product functionality to adapt to the network environment fitting the performance requirements of high-traffic website architecture and supporting unlimited concurrent processing.

Clustered deployment easily to deal with complex network environment
Centralized management ensures no major changes to the network topology while upgrading or expanding to solve problems efficiently with lower cost.

Easy operation and maintenance to reduce labor costs.
Provide an open plug-in platform to build multi-platform and multi-device security linkage, fully understand the attack logic of business.

Customized traffic analysis to solve scenario business security issues.