Full-Chain Deception: Empowering Enterprises with Proactive Defense Capabilities
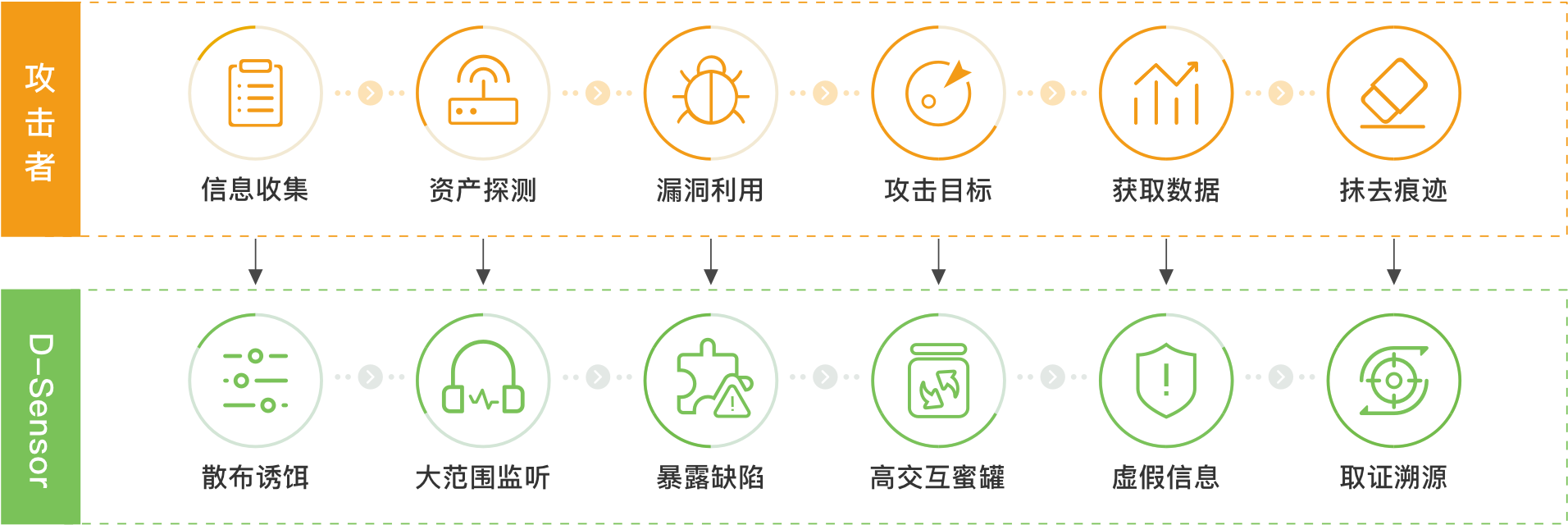
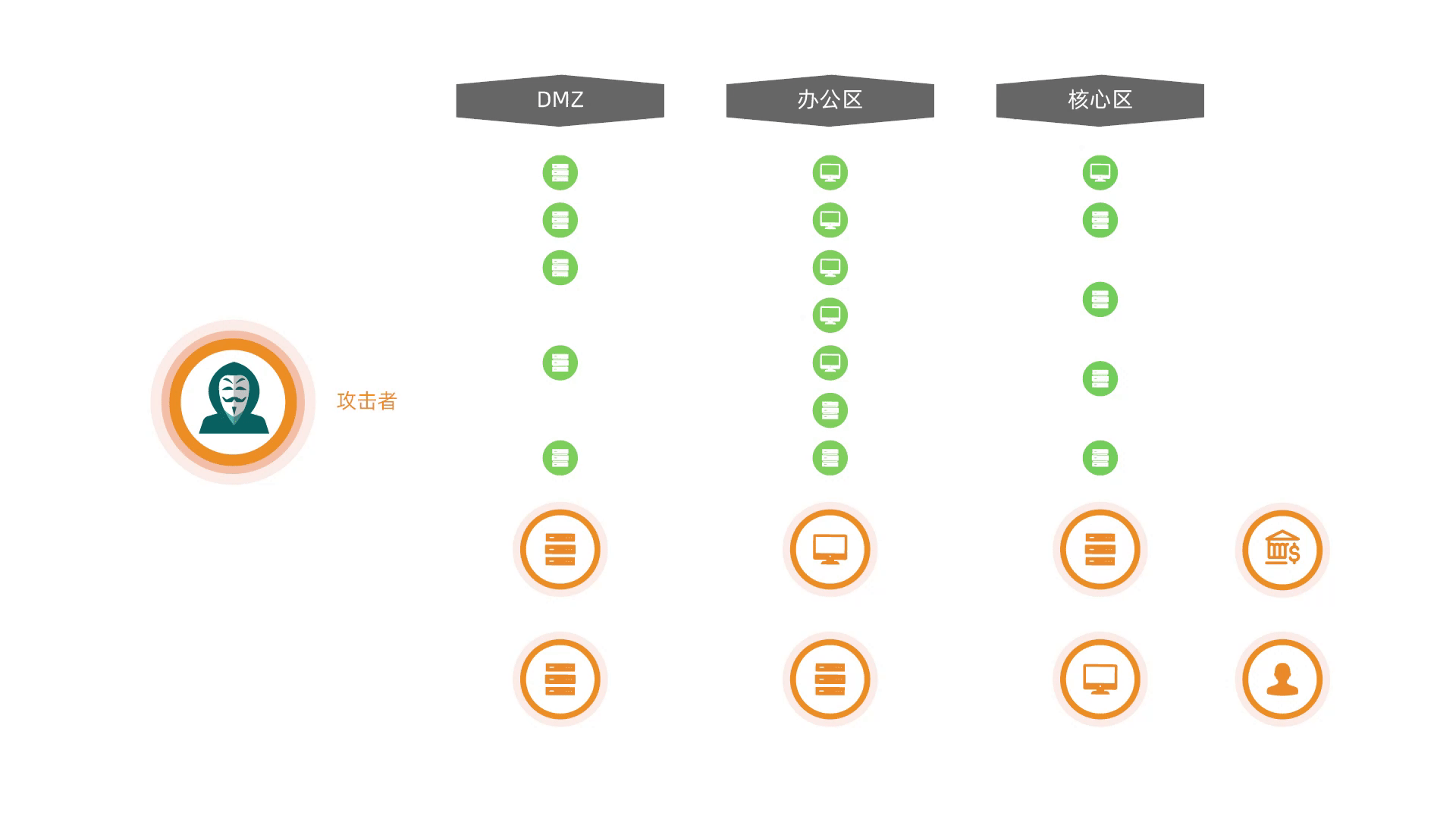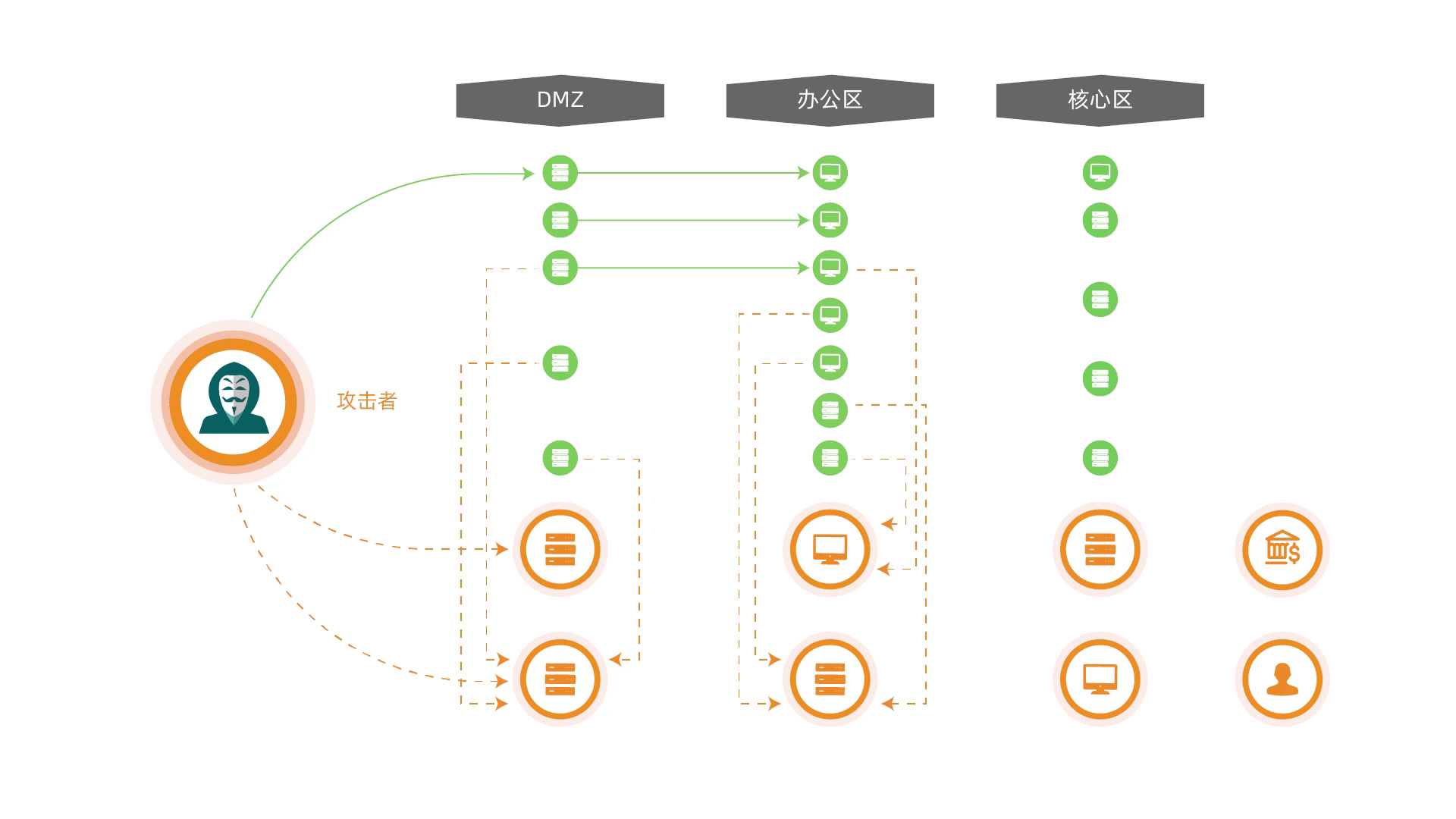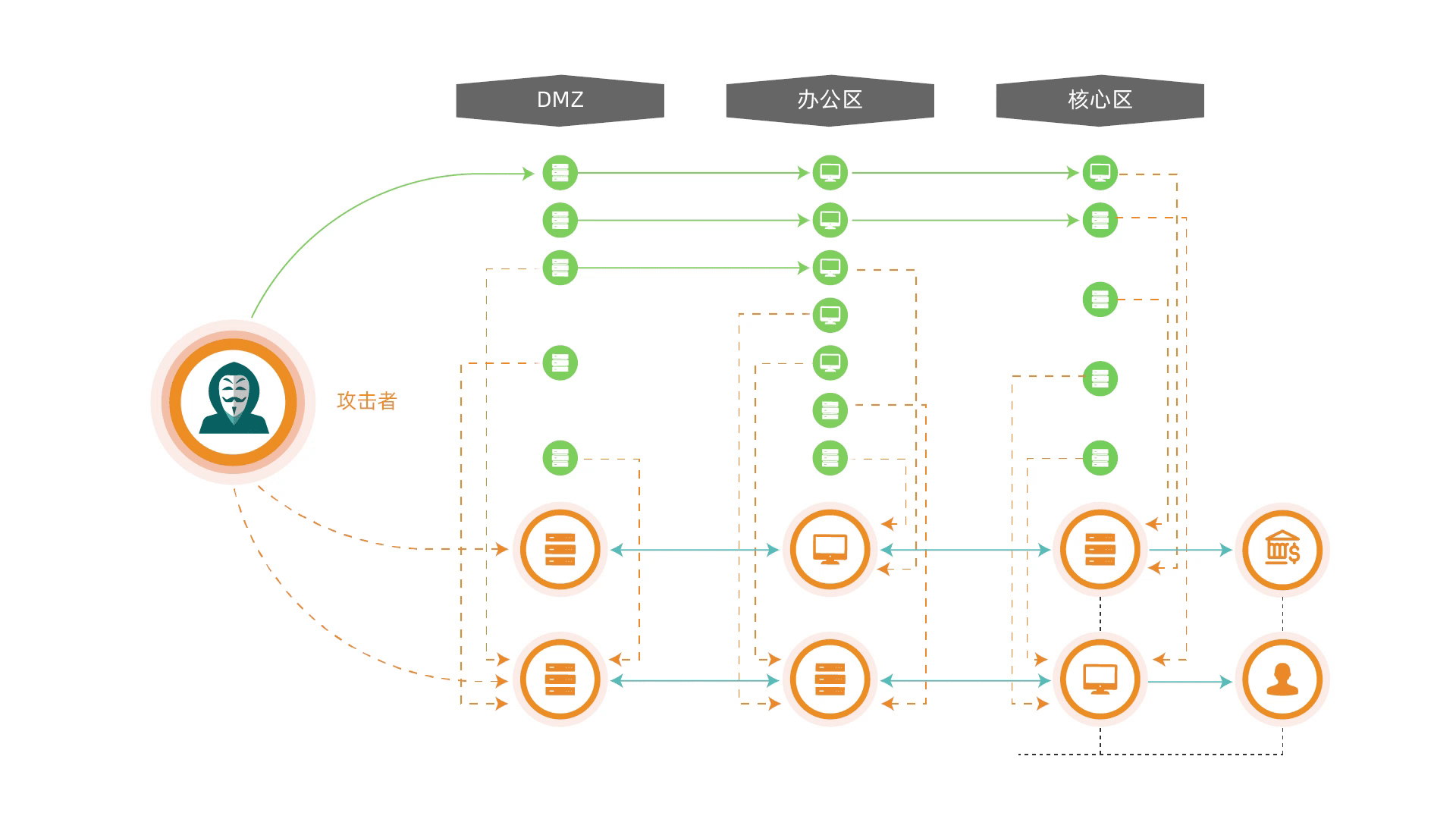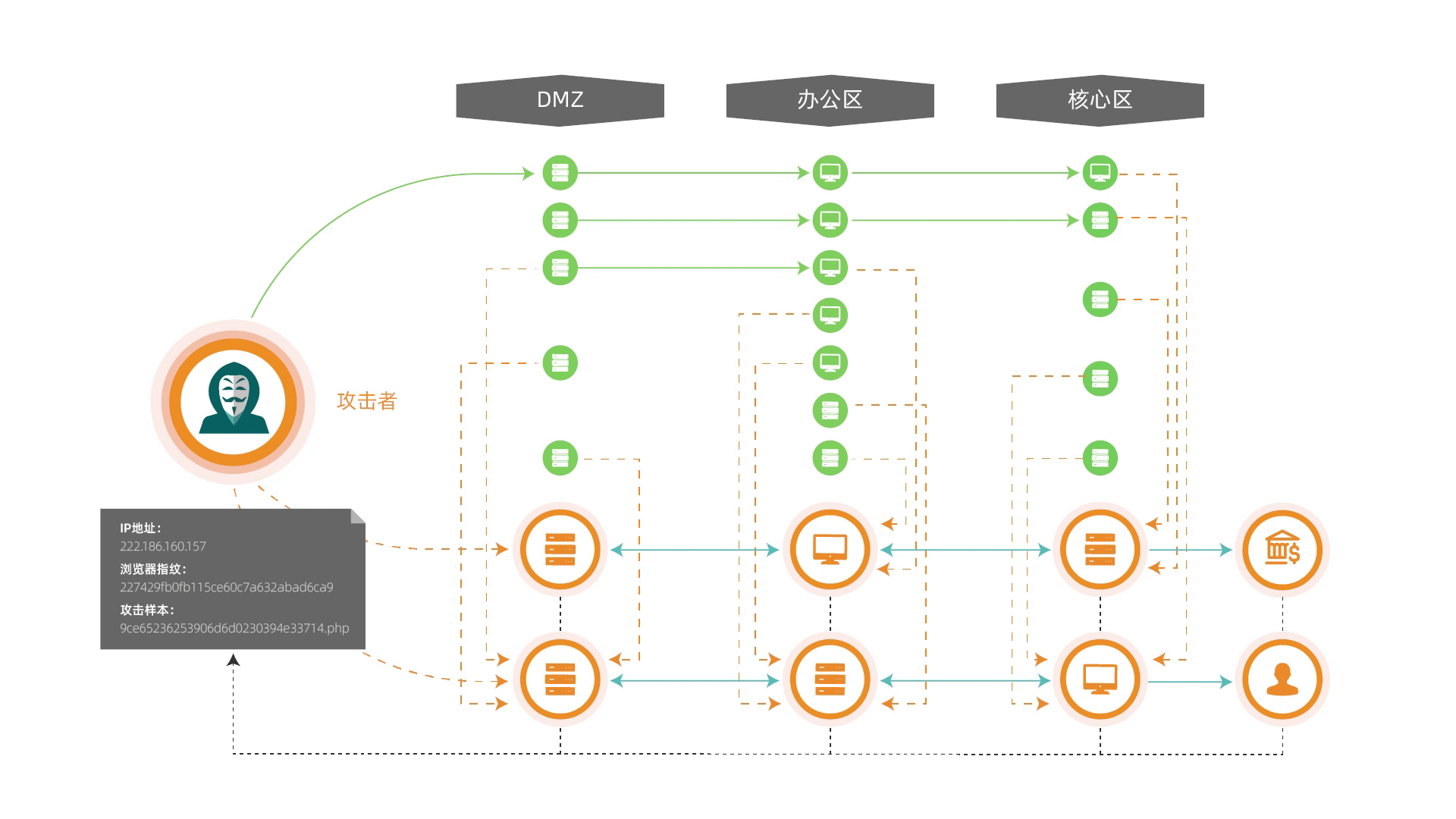
The deception system leverages advanced camouflage technologies to deploy decoys and traps along critical intrusion paths. By redirecting attackers to simulated targets while isolating real assets, while conducting forensic investigations and tracing attack origins, providing enterprises with preemptive defensive measures to safeguard real assets and enhance proactive security capabilities.
Core Capabilities
- 01
Threat Detection & Capture
Real-time monitoring of multiple IP ports enables precise detection and capture of advanced unknown threats such as 0day-based APT attacks, achieving zero false positives.
- 02
Attack Diversion & Time Manipulation
Deploying a strategic combination of decoys, vulnerabilities, and high-fidelity interactive honeypots to lure attackers toward "fake" targets, diverting attack momentum, stalling adversary dwell time, and safeguarding real assets.
- 03
Identifying Attack Techniques, Inferring Attack Intentions
The honeypot incorporates a built-in semantic analysis engine that accurately identifies attack methodologies, deduces malicious intent, and enables proactive defense measures to neutralize threats before they escalate.
- 04
Automated Forensics & Attribution
Acquiring data such as device fingerprints, social information, and location information, we rapidly sketch the attacker's profile, deliver comprehensive attack intelligence, and provide evidential support for tracing origins and apprehending attackers.
